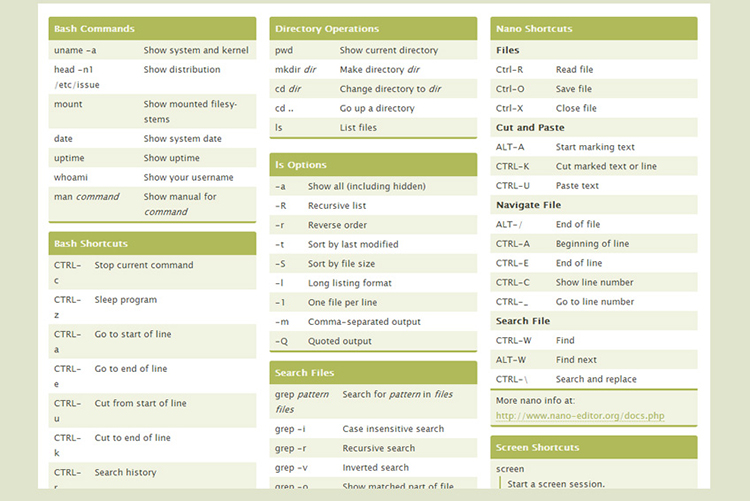
Cmd Hacking Pdf
The Portable Document Format (PDF) is a file format developed by Adobe in the 1990s to present documents, including text formatting and images.
Take advantage of this course called Download Hacking tutorial in PDF to improve your Networking skills and better understand Hacking. This course is adapted to your level as well as all Hacking pdf courses to better enrich your knowledge. All you need to do is download the training document, open it and start learning Hacking for free. List of top best cmd tricks and hacks command prompt tricks hacks tips for windows 7 8 10 PC computer all cool cmd tricks 2020 download pdf ipconfig matix net using. Jan 09, 2016 How to Hack Wi-Fi Password Using CMD Wi-Fi is the best and the easiest method to connect with the internet. Here in this article, I am going to tell you how you can hack Wi-Fi password of your friends or neighbors easily using CMD. CMD stands for Command Prompt and Command Prompt is the reliable way. NO AD-HOC OR TETHERING IS REQUIRED. Run CMD with administrator rights. Type these commands with one followed by another (i) netsh wlan set hostednetwor.
Academia.edu is a platform for academics to share research papers. CMD is a powerful tool which lets you do almost anything with your Windows PC/laptop. There are common commands like CD. And MD etc which you probably know so we won’t get into that. In this article, we have provided the best cmd commands used in hacking. Before we begin sharing the best cmd commands for hacking lets see how to enable the.
In this post, we will learn, how to hack windows using a malicious pdf file. We will use the Ngrok tool for the Port Forwarding so that we can perform this attack outside the network. If You want to Launch this attack on the same network, You can replace the LHOST and LPORT (Step 7) with Your own Local IP Address.
What Are We Covering Today?
1.Create a Malicious PDF file using Metasploit
2. Port Forwarding using Ngrok
3. Create a Listener for our Malicious Payload using Metasploit
4. Read this post on Android Hacking (Recommended)
1. Steps to create a Malicious Payload using Metasploit Framework
Step 1: Open terminal and type this command to start Metasploit Framework
Step 2: Now enter the following command to find the exploit
Step 3: There are lots of exploits available which you can try, but we will use the following one. Type the following command to use the exploit
Step 4: Now we need to specify the Payload to be Injected into PDF, for that type the following command
This will create a Reverse TCP connection to the attacker Machine
Step 5: Now start the Ngrok so that we can use the port forwarding. to launch the ngrok, type the following command
If you don’t Know about Ngrok, you can read this post. I have already explained the installation guide of Ngrok
Step 6: Once, You have started the Ngrok, the address before the colon(:) is Your LHOST and after the colon is LPORT as
In Your case, the LHOST and LPORT will be changed. Replace these in the following command with your own
Step 7: Now to set the LHOST, type the following command
Step 8: type the following command to set the LPORT
Step 9: Now set the name of the file by this command
Step 10: Now to check our options again so that whether everything is ready to go or not. for that enter the command
Step 11: Now type exploit
Metasploit has created a PDF named test.pdf that contains the Meterpeter listener. Metasploit has placed this file at /root/.msf4/local/test.pdf. Send this pdf by any method to the Victim
3. Create a Listener for our Malicious Payload using Metasploit
To create a listener for our Backdoor Connection, we need to type a bunch of commands
Cmd Hacking Pdf Tool
Step 1: Open Metasploit in a new terminal by the following command
Step 2: Now execute the following commands one by one
So as the victim opens the PDF file, a meterpreter connection will be eatablished. You can perform lots of operation after that. Just type help and there will be list of commands which you can execute
Cmd Hacking Basics Pdf
–>> You may encounter certain errors or running issues. So do not panic! Just comment your queries below or you can send your query here. We will get back to you soon!